As the end of the year draws near, the IBM X-Force research and development team takes a closer look at the security trends shaping our world. In particular, this report examines how the Internet continues to connect more people, places and things, resulting in a new range of security risks.
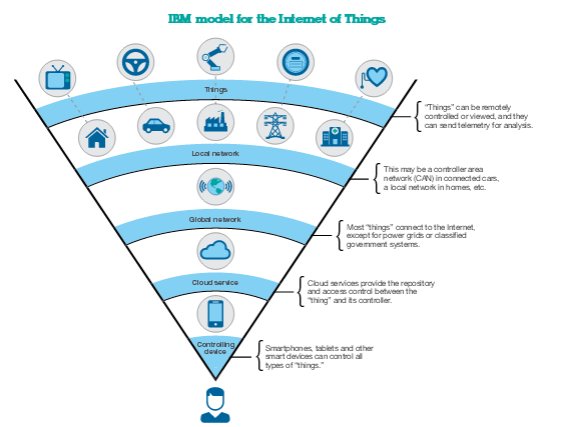
First, let’s look at security for the Internet of Things. The ubiquitous connectivity of the “things” that enrich our lives, from thermostats to automobiles to medical devices, meanssoftware development is happening adjacent to cutting-edge technology developed by hardware manufacturers. The security industry can help guide the development of security practices for embedded software from near-inception. Not only would this create a new era of secure software, it would save a world of potential breaches from impacting the Internet of Things.
This connectivity is changing the way we live and creating new questions about personal privacy, marketing and Internet security as “things” are manufactured and sold to consumers. Malicious actors intent on taking control of data, identities and passwords have been investigating and making use of Internet- connected devices that are not securely developed, making them easier targets than PCs, laptops or tablets. It’s critical now,
more than ever, for organizations and the employees utilizing this nascent technology to consider the risks as they connect to the enterprise safety zone. We’ll talk later in this report about the individual risks and protections that are available to assist in these important areas.
Next, we focus on places—specifically, those on the Internet that are unsafe. Leveraging our database of more than 23 billion URLs and IP addresses, we’ll look at which countries are prone to the highest proportion of malware and botnet infections, and how the landscape has changed over the last 14 months.
As with every IBM X-Force Threat Intelligence Quarterly, people are at the heart. As security practitioners, we hope the insights into securing things and places can be helpful for protecting your own network. We’ll be back in 2015 with a year-end review of the security trends from 2014, and what to expect in the year to come